Crypto Drainage Services: Critical Insights You Need Now

What does "crypto drainer" mean?
A crypto drain is a harmful code created with the intent of stealing cryptocurrencies from your digital wallet. It operates differently compared to conventional attacks. phishing attacks That attempts to seize login details, a crypto drain trick lures you into it. connecting your wallets , such as MetaMask or Phantom and inadvertently approving transactions that provide them entry to your finances.
Disguised as a legitimate Web3 The project explains that a crypto drainer is typically promoted through hacked social media profiles or Discord channels. If you become a victim of this scam, the drainer can immediately access your funds. move assets from the wallet .
Cryptocurrency drain attackers can appear in different guises:
・Malicious smart contracts that initiate unauthorized transfers.
・Fake NFTs Or token systems that generate deception exchanges or assets.
Cryptocurrency drain attacks are an increasing menace in Web3, facilitating swift, automated theft of digital tokens from unaware users via deceit. Here are some typical tactics employed by these attackers: 1. Phishing scams designed to steal private keys. 2. Malware infections targeting cryptocurrency wallets. 3. Fake websites mimicking legitimate exchanges or wallet services.
・Phishing websites.
・Fake airdrops .
・Deceptive ads.
・Malicious smart contracts.
・Harmful browser extensions.
・Fake NFT marketplaces.
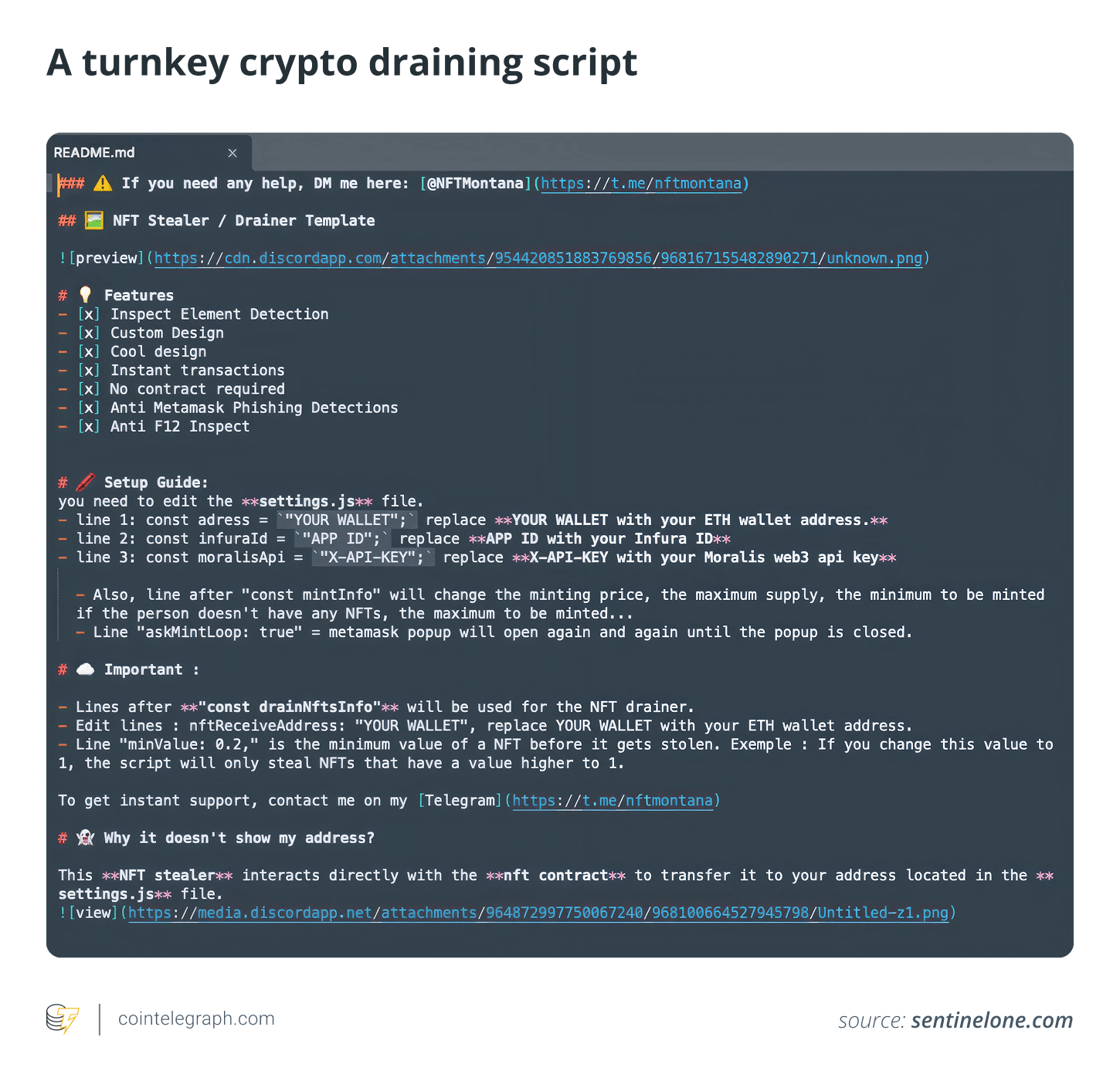
Crypto drainers-as-a-service (DaaS), explained
DaaS increases the risk of crypto drain attacks by making them commercially viable. Similar to SaaS platforms, DaaS providers offer readily available solutions for these purposes. malware kits to cybercriminals , frequently in return for a cut of the illicitly obtained money.
In the DaaS framework, developers provide ready-to-use draining scripts, adjustable phishing tools, and assistance with integration in return for a portion of the illicit gains. A DaaS package could include additional elements such as social engineering guidance, privacy protection services, and frequent updates, which make these offers appealing even to those with minimal expertise in scam operations.
Kinds of cryptocurrency Data as a Service solutions encompass:
・ JavaScript-based drainers: Harmful JavaScript gets inserted into phishing sites that imitate genuine ones. decentralized apps (DApps) These scripts run when you link your wallet, quietly initiating approval transactions that result in asset drainage.
・ Token approval malware: Deceives users into providing unrestricted token access through harmful smart contracts.
・ Clipboard hijackers: Hacker employ clipboard hijackers to track and substitute copied wallet addresses with ones managed by attackers.
・ Info-stealers: They harvest browser data, wallet extensions and private keys . Some DaaS packages combine these with loader malware that drops additional payloads or updates the malicious code.
・ Modular drainer kits: Segregated into modules, these drainers use obfuscation techniques to bypass browser-based security tools.
Did you know? According to Scam Sniffer, phishing campaigns using wallet drainers siphoned off over $295 million in NFTs and tokens from unsuspecting users in 2023.
What crypto DaaS kits include
Crypto DaaS packages are ready-to-use toolkits offered for sale to scammers This allows individuals to pilfer digital assets even without much technical expertise. Such toolkits often come equipped with phishing webpage designs, harmful smart contracts, wallet-siphoning scripts, among other components.
Here’s what typically comes with crypto DaaS solutions:
・ Pre-built drainer software: Plug-and-play malware that needs little configuration.
・ Phishing kits: DaaS providers offer adaptable phishing website templates that hackers can alter based on their schemes.
・ Social engineering: Through Desktop as a Service, cyber attackers discover assistance. social engineering Along with strategies aimed at manipulating users into linking their wallets.
・ Operational security (OPSEC) tools: To evade discovery, certain DaaS providers supply sophisticated operational security measures. mask user identity and hide digital footprints.
・ Integration assistance and/obfuscation: These services assist attackers in deploying drainer scripts effortlessly and employ obfuscation tools to avoid detection.
・ Regular updates: Regular updates aim to circumvent financial security measures and surveillance tools.
・ User-friendly dashboards: Dashboards that enable hackers to manage activities and track transferred funds.
・ Documentation and tutorials: Detailed guidelines designed to help newcomers carry out deceptive practices effectively.
・ Customer support: Some DaaS operators provide real-time help through secure messaging apps like Telegram .
For as low as $100 to $500, DaaS solutions can be purchased outright, or you can opt for subscription-based models. sophisticated crypto attacks are no longer restricted to seasoned hackers. Even newcomers can obtain these scripts with minimal funding, essentially making this more accessible to everyone. type of crime .
Did you know? Sophisticated DaaS instruments frequently refresh their code to bypass recognition from web add-ons such as WalletGuard and safety warnings released by MetaMask. Trust Wallet .
Development of cryptocurrency draining as a prevalent scam tactic
The threat landscape of cryptocurrency fraud is constantly evolving. Emerging around 2021, crypto drainers have rapidly transformed the landscape. Their ability to stealthily siphon funds from users' wallets has made them a threat that demands vigilance.
Drainers specifically designed to target MetaMask began to emerge around 2021 and were openly advertised on illicit online forums and marketplaces.
Here are some prominent drainers that have been around for some time:
・ Chick Drainer: It appeared in late 2023, focusing on Solana ( SOL ) users through phishing campaigns. It operates using the CLINKSINK script, embedded in fake airdrop websites.
・ Rainbow Drainer: The platform exhibits coding parallels with Chick Drainer, indicating possible recycling of code or cooperation between malicious parties.
・ Angel Drainer: Introduced approximately in August 2023, Angel Drainer has been heavily advertised on Telegram by hacker collectives such as GhostSec. Scam affiliates must initially shell out anywhere from $5,000 to $10,000 and additionally fork over a 20% cut of every asset they manage to steal using this tool.
・ Rugging’s Drainer: This data-as-a-service (DaaS) drainer works with multiple cryptocurrency platforms and charges relatively modest commission fees, usually between 5% to 10% of the funds that have been siphoned off.
Following the breach of the U.S. Securities and Exchange Commission’s X account in January 2024, Chainalysis found A crypto drain operation mimicking the SEC prompted users to link their wallets in hopes of receiving non-existent airdropped tokens.

As per the Kasperksy Security Bulletin, dark web discussions discussing Crypto draining incidents surged significantly in 2024, increasing by 135% to reach 129 discussions from just 55 instances in 2022. The topics covered in these exchanges include purchasing and vending harmful programs as well as assembling dissemination groups.
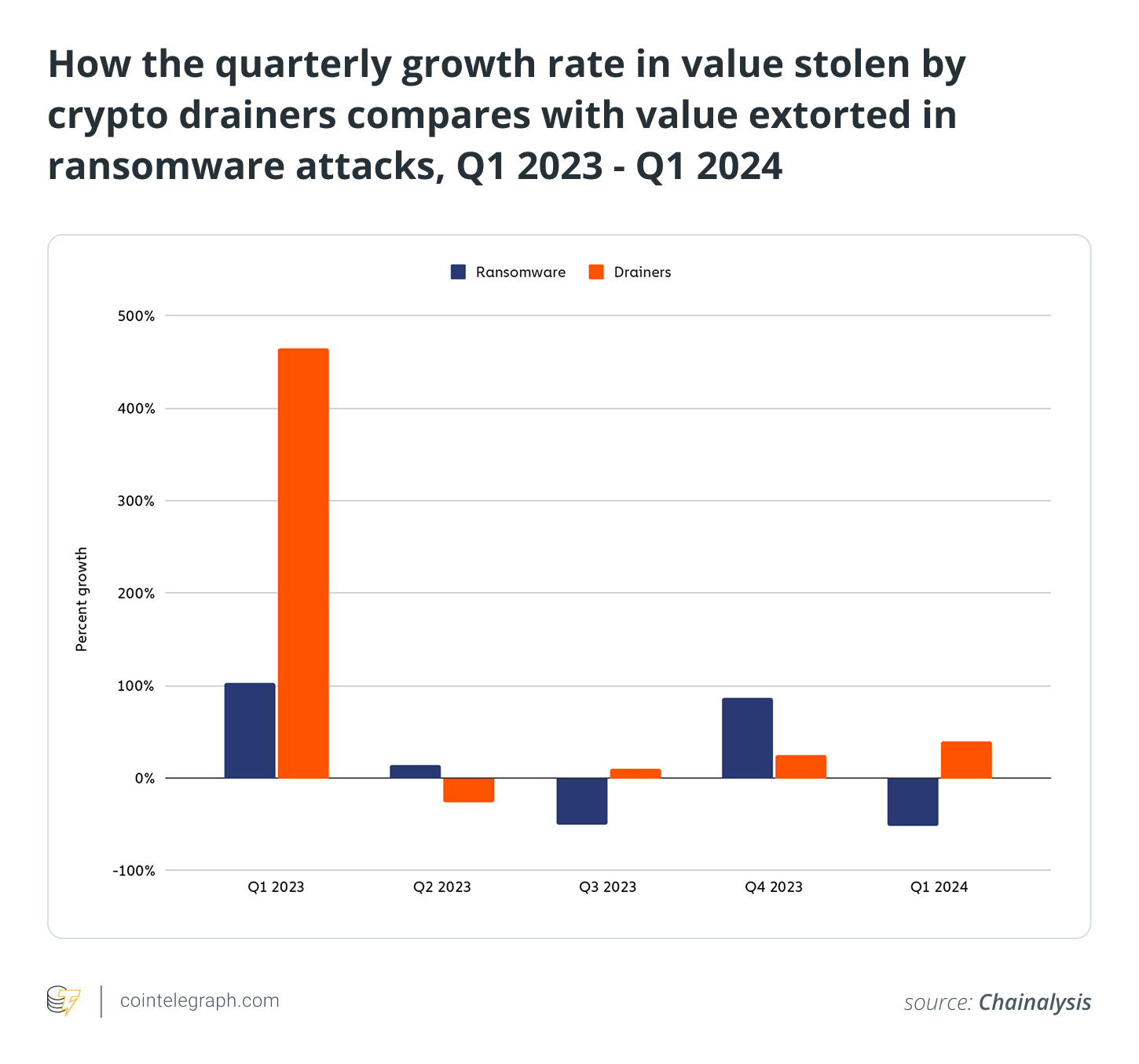
As the subsequent graph shows, crypto drainers have been pilfering cryptocurrency at an accelerating quarterly pace that surpasses even that of ransomware.
Indicators to spot a cryptocurrency DaaS assault
Identifying a cryptocurrency wallet draining attack promptly is essential for reducing possible financial loss and safeguarding your funds. It’s important to exercise caution since an advanced drain attack might bypass typical warning systems. Even when using automatic tools, you should stay watchful.
Below are some signs that your wallet might be at risk:
・ Unusual transactions: A warning sign of a draining attack is spotting unauthorized transactions. Such activities can involve unforeseen token moves or withdrawals to unfamiliar wallet addresses. In some cases, hackers perform several minor transfers to stay under the radar, making it crucial to keep an eye out for recurring such incidents. atypical activities involving small-scale cryptocurrencytransactions .
・ Lost access to wallet: If you're unable to reach your wallet or find your funds gone, this might indicate that an attacker has seized control. Such incidents commonly occur when the perpetrator alters the private keys or recovery phrases, thereby preventing you from accessing your assets.
・ Security notifications from payment apps: Your cryptocurrency wallet might send you security notifications for unusual activities such as sign-ins from unfamiliar devices, unsuccessful login tries, or illicit financial transactions. Such alerts suggest that an unauthorized individual could be attempting to gain entry into your wallet or might have already done so.
・ Inauthentic project websites or decentralized applications (DApps): If you come across a replicated or recently released platform imitating an authentic Web3 service and asking for wallet connections, this should raise suspicion as a potential crypto siphon. Such platforms may include pressing appeals to act quickly, encouraging users to instantly claim rewards, airdrops, or mint NFTs. This urgency aims to push people into linking their wallets before they can confirm whether the site is genuine.
・ Unverified social media promotions: Links that seem suspicious and are circulated through platforms like X, Discord, Telegram, or Reddit, frequently coming from unverified user profiles, typically signal an attempted fraud aimed at siphoning funds from wallets. Scammers might exploit hacked accounts for distributing these harmful links as well.
・ Unaudited smart contracts: Engaging with unknown smart contract code lacking public audits or GitHub openness might put your digital wallets at risk of encountering concealed drain scripts.
・ Wallet prompts requesting broad permissions: Requests for sign-in or approval that seek complete token expenditure rights or access to all assets instead of particular transactions should be considered significant red flags.
Did you know? Just one popular drainer kit can be used by hundreds of affiliates. That means a single DaaS platform can be behind thousands of wallet thefts in a matter of days.
How to protect your crypto wallet from DaaS attackers
To protect your crypto wallet from DaaS attackers, adopting strong, proactive security practices is essential. Blockchain monitoring tools can help identify suspicious patterns linked to drainer activity, allowing you to respond quickly.
Here are key strategies to help protect your digital assets:
・ Use hardware wallets: Hardware wallets Cold wallets keep private keys offline, protecting them from online dangers such as malware and phishing attempts. Storing your keys on a physical device greatly reduces the chances of remote hacking and is perfect for safeguarding cryptocurrency over the long term.
・ Enable 2FA (two-factor authentication): Adding two-factor authentication to your wallet This means that even if someone obtains your password, they still require an additional authentication step. They must enter a verification code sent to your mobile device to gain entry into the account, alongside your password, which significantly complicates unauthorized access.
・ Avoid phishing links: Always double-check web addresses and steer clear of clicking on unexpected messages about prizes or upgrades. Do not enter your private keys or seed phrases On dubious websites. If unsure, type the accurate web address directly.
・ Protect your private keys and seed phrases: Keep your private keys and seed phrases stored securely offline in a tangible place. Avoid saving this information on devices connected to the internet; otherwise, hackers could potentially gain access to them, thus endangering your wallet.
・ Confirm applications and web browser add-ons: Ensure you install software exclusively from official sources. Prior to downloading, investigate the applications to steer clear of potentially harmful or counterfeit tools.
・ Monitor wallet activity regularly: Examine your wallet for any unapproved transactions or strange activity. Detecting these early can aid in preventing additional financial loss and enhance the likelihood of recovering what was taken.
What actions should you take if you're hit with a crypto-drainer assault?
Immediate steps must be taken if you believe your cryptocurrency wallet has been hacked. Even though recovering funds is uncommon, prompt action can help prevent additional losses.
Here are the actions you should follow If you experience a cryptocurrency as-a-service attack:
・ Secure your accounts: Promptly update the password for your wallet and activate 2FA if you can still get into it. Move whatever funds are left to a safe, unbreached wallet.
・ Notify your wallet provider or exchange: Report the incident to your wallet provider or exchange. You could request them to monitor your account or freeze suspicious activity. Platforms may flag suspicious addresses or prevent further transfers.
・ File a report with authorities: Reach out to your local police department or cybercrime division, since stealing cryptocurrencies is generally considered a financial crime.
・ Seek professional assistance: Blockchain forensic cybersecurity companies have the capability to examine transactions and possibly track down the misappropriated funds. However, complete retrieval is improbable, particularly if the assets have been moved through various channels. mixers or bridges Expert assistance might enhance investigations.
Post a Comment for "Crypto Drainage Services: Critical Insights You Need Now"
Post a Comment